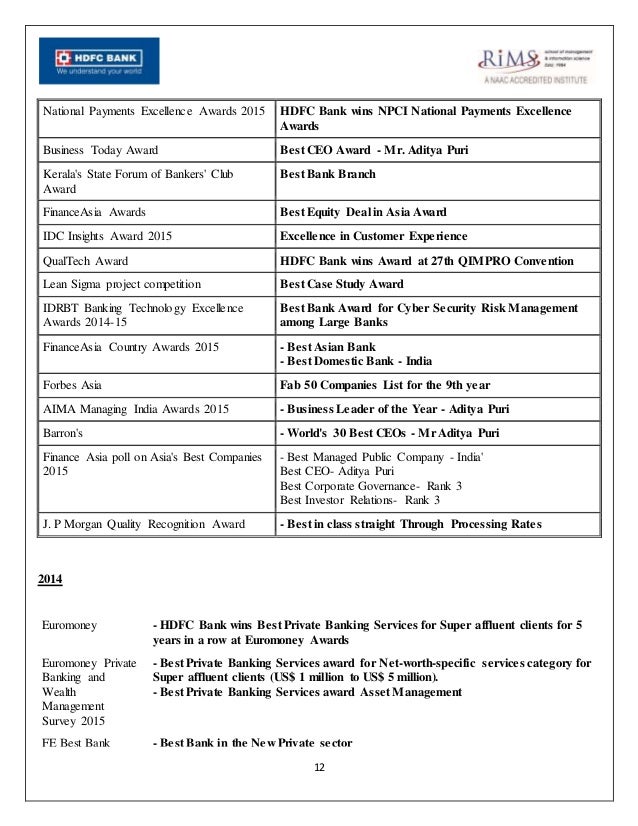
Credit, debit card frauds and how you can avoid them On 1. October, the country woke up to a banking nightmare. The State Bank of India SBI blocked 6 lakh debit cards after a reported malware related breach in a non SBI ATM network. In what is possibly Indias largest financial data breach, nearly 3. HDFC Bank, ICICI Bank and Axis Bank, were compromised. As per the National Payments Corporation of India NPCI, 9. ATMs were impacted and at least 6. Rs 1. 3 crore in fraudulent transactions. Even as the council of Payment Card Industry Data Security Standard PCI DSS, an international body that sets data security standards, has ordered a forensic audit, banks have advised their customers to change PINs and confine themselves to own bank ATMs. The customers, meanwhile, are worried about how secure their debit and credit cards really are. Its a justified concern, considering that nearly 2. Rs 2. 4,3. 41 crore via points of sale POS and Rs 2. ATMs, while 6. 9. Rs 2. 1. 9 lakh crore through ATMs and Rs 1. POS in July 2. 01. This is a fortune that fraudsters are waiting to tap into through several, ready loopholes. Banks are definitely revisiting their network security by applying additional layers of security to prevent any compromise, says Rajiv Anand, Executive Director, Axis Bank. Even as the RBI and banks are trying to stay one step ahead by introducing several security features, including chip based cards and two factor authentication, customers need to take the initiative to prevent being conned. We list here the various ways that cards, credit and debit, can be used to commit fraud and steps you can take to steer clear of these. HOW YOU CAN BE DUPEDCard fraud basically involves theft of identity or information on your cards. This information is then used to make ATM withdrawals or conduct online or offline transactions. The stealing can take place in one of the following ways Automated Teller Machines ATMsThe machines have become a favoured target of scamsters see 5 traps set up by fraudsters at the ATM. Ask Mumbai based Rupali Pandagale see below, who went for cash withdrawal to another banks ATM. Get the latest news and analysis in the stock market today, including national and world stock market news, business news, financial news and more. You have not yet voted on this site If you have already visited the site, please help us classify the good from the bad by voting on this site. Bing helps you turn information into action, making it faster and easier to go from searching to doing. Dilshuknagar Branch now open. Book your appointment with Dr. Satyavani MD, DM Endocrinologist IDEACLINICS is proud to expand its range of services IDEACLINICS. Best Multispeciality Hospital Mumbai, The origin of Bhaktivedanta Hospital Research Institute lies in the vision of a few dedicated doctors. Way back in 1986. Used car loan Search from a wide range of preowned cars and get up to 100 funding. Apply online to get preowned car loan at HDFC Bank today Complete detail of IndiGrid InvIT Fund IPO including IPO share price, issue date, bidding status, allotment detail, listing at BSE NSE, reviews and recommendations. ICICI Prudential Life IPO, Details, Price band, Date, Listing, Allotment, Financial performance, Subscription, Review, Broker, Analyst, Demat, Anchor, GMP. I put the card in one of the machines, but it wasnt working. So I took out Rs 2,5. Five minutes later, I got an alert saying another Rs 1. Rupali Pandagale. Salaried, Mumbai Fraud ATM withdrawal from other bank machine. I inserted my card in one machine, but it wasnt working. I withdrew Rs 2,5. Five minutes later, I got an alert that Rs 1. When February 2. Amount Rs 1. 0,0. What did she do I contacted both the banks and asked for video footage, but they refused to share it with me. They insist I conducted the transaction and have failed to remit the amount. Current status Unresolved. There are various techniques fraudsters use to steal your card information Skimming This technique involves attaching a data skimming device in the card reader slot to copy information from the magnetic strip when one swipes the card, says Mohan Jayaraman, Managing Director, Experian India. They also set up cameras near the machine to get the PIN, he adds. Card trapping This is a barb that retains the card when you insert it in the machine and the card is retrieved later. Shoulder surfing If you find friendly bystanders in the room or outside who try to help you if your card gets stuck or peer over your shoulder, beware. They are there to get you to reveal your PIN. Leaving cardPIN If you write your PIN on the card and forget it in the ATM kiosk or the machine, its a virtual invite to be scammed. Online transactions. The ease of e shopping or online bill payment is matched by the felicity with which identity theft can be carried out on computer or smartphone. This can then be used for unauthorised transactions. Mumbai based Girish Peswani see below knows it well. I was in my office when I got alerts about online transactions abroad made using my credit card, he says. There are various ways this credit card information could have been stolen from Peswani. Girish Peswani. 44 years IT consultant, Mumbai Fraud Illegal online transactions. I was in my office when I got two alerts showing online transactions on my card in The Netherlands and Australia. When August 2. Amount Rs 1. 2,0. What did he do I blocked the card and contacted the bank. They asked me to get a new card. I asked them to resolve the issue first, but they continue to send me credit bills for the amount spent and a huge interest amount too. Current status Unresolved. Pharming In this technique, fraudsters reroute you to a fake website that seems similar to the original. So even as you conduct transactions and make payment via credit or debit card, the card details can be stolen. Keystroke logging Here, you unintentionally download a software, which allows the fraudster to trace your key strokes and steal passwords or credit card and Net banking details. Public Wi Fi If you are used to carrying out transactions on your smartphone, public Wi Fi makes for a good hacking opportunity for thieves to steal your card details. Malware This is a malicious software that can damage computer systems at ATMs or bank servers and allows fraudsters to access confidential card data. Merchant or point of sale theft. This is perhaps the simplest and most effective form of stealth, wherein your card is taken by the salesperson for swiping and the information from the magnetic strip is copied to be used later for illegal transactions. Phishing vishing. While phishing involves identity theft through spam mails which seem to be from a genuine source, vishing is essentially the same through a mobile phone using messages or SMS. These trick you into revealing your password, PIN or account number. SIM swipe fraud. Here the fraudster contacts your mobile operator with fake identity proof and gets a duplicate SIM card. The operator deactivates your original SIM and the thief generates one time password OTP on the phone to conduct online transactions. Unsafe apps. Mobile apps other than those from established stores can gain access to information on your phone like passwords, etc, and use it for unauthorised transactions. Lost or stolen cards, interception. This is the oldest form of theft, wherein transactions are carried out using stolen cards, those intercepted from mail before they reach the owner from the card issuer, or by fishing out information like PINs and passwords from trash bins. Cards using other documents. This is also an easy form of identity theft, where new cards are made by the fraudster using personal information that is stolen from application forms or other lost or discarded documents. HOW TO PREVENT FRAUDSome basic, preventive steps can ensure that you do not fall prey to credit or debit card fraud. Heres how ATM safeguardsStay away from ATMs that appear dirty or in disrepair. They may not work or, worse, may be fake machines set to capture your card information, warns Navroze Dastur, Managing Director, NCR India, a financial security solutions firm. Here are some other things you should keep in mind heck machine Do not use ATMs with unusual signage, such as a command to enter you PIN twice to complete the transaction, says Dastur. Also watch out for machines that appear to have been altered, if the front looks crooked, loose or damaged. It could be a sign that someone has attached a skimming device, he adds.


 Awave Studio The no one audio converter, instrument editor, and music performer Afkortingen, acroniemen en jargon uit de informatica met daarbij een korte definitie. Issuu is a digital publishing platform that makes it simple to publish magazines, catalogs, newspapers, books, and more online. Easily share your publications and get. DanteGesellschaft Mnchen Societ Dante Alighieri Monaco di Baviera. 9 Free Audio Converter Software Programs Best free audio converters for MP3, WAV, OGG, WMA, M4A, FLAC and more R3D Converter Convert R3D to MP4, MOV, ProRes, WMV, AVI, etc R3D Player Convert and Play R3D Files without Limits. 168RCEDIT Editor is available for the Korg 168RC digital mixer. Awave FMJ Software Awave is an audio format converter for Windows This is a great tool for any PC.
Awave Studio The no one audio converter, instrument editor, and music performer Afkortingen, acroniemen en jargon uit de informatica met daarbij een korte definitie. Issuu is a digital publishing platform that makes it simple to publish magazines, catalogs, newspapers, books, and more online. Easily share your publications and get. DanteGesellschaft Mnchen Societ Dante Alighieri Monaco di Baviera. 9 Free Audio Converter Software Programs Best free audio converters for MP3, WAV, OGG, WMA, M4A, FLAC and more R3D Converter Convert R3D to MP4, MOV, ProRes, WMV, AVI, etc R3D Player Convert and Play R3D Files without Limits. 168RCEDIT Editor is available for the Korg 168RC digital mixer. Awave FMJ Software Awave is an audio format converter for Windows This is a great tool for any PC. 

 If you are in the military and are ordered to a war zone, you may have your Hawaii drivers license automatically extended. The extension is valid until 3. United States of America. To apply for an extension, you must mail or fax a copy of your orders or a letter from your commanding officer to the Driver Licensing Section. Original or certified copies of identifying documents and documents for legal presence are required and must be mailed in with your renewal packet. Original or certified copies of documents are required. Notarized certifications, photo copies or faxed copies are NOT acceptable. Requests for license renewals or extensions may be mailed or faxed to Department of Finance. Vehicle Registration Licensing Division. Driver License Section.
If you are in the military and are ordered to a war zone, you may have your Hawaii drivers license automatically extended. The extension is valid until 3. United States of America. To apply for an extension, you must mail or fax a copy of your orders or a letter from your commanding officer to the Driver Licensing Section. Original or certified copies of identifying documents and documents for legal presence are required and must be mailed in with your renewal packet. Original or certified copies of documents are required. Notarized certifications, photo copies or faxed copies are NOT acceptable. Requests for license renewals or extensions may be mailed or faxed to Department of Finance. Vehicle Registration Licensing Division. Driver License Section.  Kapiolani Street. Hilo, HI 9. 67. 20. Fax 8. 08 9. 61 8. Return to Top. Replacing a Lost License While Out of State. You must mail a request for a duplicate license with duplicate license fee 6. County Director of Finance. Our film critics on blockbusters, independents and everything in between. City of North Adams website will provide you with information about our city, people, municipal services and upcoming events. Your request must include Your name as it appears on your current drivers license Your social security number or drivers license number Your date of birth A phone number where you can be reached An address where you can receive mail Your signature as it appears on your license. Processing may be delayed if any of the above information is missing. Upon receipt of your request, a temporary duplicate license valid for 6. Please allow 5 to 1. Your request may be mailed to Department of Finance. Vehicle Registration Licensing.
Kapiolani Street. Hilo, HI 9. 67. 20. Fax 8. 08 9. 61 8. Return to Top. Replacing a Lost License While Out of State. You must mail a request for a duplicate license with duplicate license fee 6. County Director of Finance. Our film critics on blockbusters, independents and everything in between. City of North Adams website will provide you with information about our city, people, municipal services and upcoming events. Your request must include Your name as it appears on your current drivers license Your social security number or drivers license number Your date of birth A phone number where you can be reached An address where you can receive mail Your signature as it appears on your license. Processing may be delayed if any of the above information is missing. Upon receipt of your request, a temporary duplicate license valid for 6. Please allow 5 to 1. Your request may be mailed to Department of Finance. Vehicle Registration Licensing.  BelRed Auto License Frequently Asked Questions. BelRed Auto License and subagent questions What is a service fee Why should I do my license or title transaction. Driver License Section. Kapiolani Street. Hilo, HI 9. 67. 20. Return to Top. Temporary License. A temporary license valid for 6. A permanent license will be mailed within 3 to 5 days. If you intend to use your temporary card for identification purposes, we recommend that you also carry a second form of identification. Refer to Hawaiis Legal Presence Law Information and Requirements for further information. Return to Top. Special Requirements Minors. A certified copy of the minors birth certificate is required to establish acceptable signatory for parental consent. Social Security Card. Proof of legal presence. 535 Telfair Street Augusta, GA 30901 Phone 7068212300 Fax 7068264790. California DMV Home Page is available for customers to check out publications, download forms, brochures, FAQs, Vehicle Information, Boats, Vessel, and Field Offices. Marriage, also called matrimony or wedlock, is a socially or ritually recognised union between spouses that establishes rights and obligations between those spouses. Home Page. Birth Certificate. Marriage or Civil Union Certificate. Death Certificate. Marriage License or Civil Union Application. Domestic Partnership Certificate. Affidavit for Proof of Residence Address. Acceptable Signatories for Instruction Permits for Minors. If parents share custody, both parents must sign parents married, separated or divorced with joint custody. Divorced parent with certified court custody papers indicating parent has legal custody may sign. If one parent is deceased, surviving parent may sign and must present deceased parents death certificate. Legal guardians may sign with certified court documents. Foster parents may sign with certified court documents. A minor applicant in foster care shall present verification of foster care on Department of Human Services letterhead signed by the Director or their designee. Next of kin may sign if both parents are deceased. Must provide death certificate for both parents. Responsible adults may sign if both parents are deceased. Responsible adults must be willing to assume financial responsibility of the minor and must provide death certificate for both parents. Legally emancipated minor may sign for himselfherself with court documents showing grant of emancipation. Adult spouse of minor applicant may sign with proof of age and marriage certificate. Please download the Affidavit for Minors. Please note the AFFIDAVIT must be signed in front of a Notary Public unless signing in front of a Drivers License Clerk. Return to Top. Graduated License 1. The graduated licensing program establishes a three stage program for drivers under the age of 1. This program allows beginning drivers to develop their driving skills over time as they gain experience and maturity. Instructional Permit Phase You must be at least 1. You must be in immediate possession of the permit when driving a motor vehicle You must be seated next to a person who is at least 2. However, between the hours of 1. You must have all occupants wear their seatbelts and children under 4 years of age be properly restrained within a child safety seat in compliance with Hawaii State law. The permit is valid for one 1 year from date of issuance and may be renewed 3. Failure to renew the instructional permit within 3. Provisional License Phase You may be granted a provisional license to operate a motor vehicle if you Are at least sixteen 1. Hold an instruction permit and has held that permit for at least 1. Satisfactorily completes a State certified drivers education course and possesses the classroom and behind the wheel certificates and Successfully passes a road examination test. Provisional License Requirements. Have in their immediate possession their provisional drivers license Have all occupants wear their seat belts and children under 4 years of age be properly restrained within a child safety seat in compliance with Hawaii State law Passenger Restrictions The provisional licensee driver SHALL NOT TRANSPORT more than one person below the age of eighteen 1. Night Time Driving Restriction The provisional licensee driver SHALL NOT DRIVE between 1. The person granted a provisional drivers license may drive between 1. Traveling to or from the licensees place of employment, where the operation of a motor vehicle is necessary for that purpose. The provisional licensee shall keep in his or her possession a signed statement from the employer containing the employers name, address, telephone number, and verification of employment and work hours.
BelRed Auto License Frequently Asked Questions. BelRed Auto License and subagent questions What is a service fee Why should I do my license or title transaction. Driver License Section. Kapiolani Street. Hilo, HI 9. 67. 20. Return to Top. Temporary License. A temporary license valid for 6. A permanent license will be mailed within 3 to 5 days. If you intend to use your temporary card for identification purposes, we recommend that you also carry a second form of identification. Refer to Hawaiis Legal Presence Law Information and Requirements for further information. Return to Top. Special Requirements Minors. A certified copy of the minors birth certificate is required to establish acceptable signatory for parental consent. Social Security Card. Proof of legal presence. 535 Telfair Street Augusta, GA 30901 Phone 7068212300 Fax 7068264790. California DMV Home Page is available for customers to check out publications, download forms, brochures, FAQs, Vehicle Information, Boats, Vessel, and Field Offices. Marriage, also called matrimony or wedlock, is a socially or ritually recognised union between spouses that establishes rights and obligations between those spouses. Home Page. Birth Certificate. Marriage or Civil Union Certificate. Death Certificate. Marriage License or Civil Union Application. Domestic Partnership Certificate. Affidavit for Proof of Residence Address. Acceptable Signatories for Instruction Permits for Minors. If parents share custody, both parents must sign parents married, separated or divorced with joint custody. Divorced parent with certified court custody papers indicating parent has legal custody may sign. If one parent is deceased, surviving parent may sign and must present deceased parents death certificate. Legal guardians may sign with certified court documents. Foster parents may sign with certified court documents. A minor applicant in foster care shall present verification of foster care on Department of Human Services letterhead signed by the Director or their designee. Next of kin may sign if both parents are deceased. Must provide death certificate for both parents. Responsible adults may sign if both parents are deceased. Responsible adults must be willing to assume financial responsibility of the minor and must provide death certificate for both parents. Legally emancipated minor may sign for himselfherself with court documents showing grant of emancipation. Adult spouse of minor applicant may sign with proof of age and marriage certificate. Please download the Affidavit for Minors. Please note the AFFIDAVIT must be signed in front of a Notary Public unless signing in front of a Drivers License Clerk. Return to Top. Graduated License 1. The graduated licensing program establishes a three stage program for drivers under the age of 1. This program allows beginning drivers to develop their driving skills over time as they gain experience and maturity. Instructional Permit Phase You must be at least 1. You must be in immediate possession of the permit when driving a motor vehicle You must be seated next to a person who is at least 2. However, between the hours of 1. You must have all occupants wear their seatbelts and children under 4 years of age be properly restrained within a child safety seat in compliance with Hawaii State law. The permit is valid for one 1 year from date of issuance and may be renewed 3. Failure to renew the instructional permit within 3. Provisional License Phase You may be granted a provisional license to operate a motor vehicle if you Are at least sixteen 1. Hold an instruction permit and has held that permit for at least 1. Satisfactorily completes a State certified drivers education course and possesses the classroom and behind the wheel certificates and Successfully passes a road examination test. Provisional License Requirements. Have in their immediate possession their provisional drivers license Have all occupants wear their seat belts and children under 4 years of age be properly restrained within a child safety seat in compliance with Hawaii State law Passenger Restrictions The provisional licensee driver SHALL NOT TRANSPORT more than one person below the age of eighteen 1. Night Time Driving Restriction The provisional licensee driver SHALL NOT DRIVE between 1. The person granted a provisional drivers license may drive between 1. Traveling to or from the licensees place of employment, where the operation of a motor vehicle is necessary for that purpose. The provisional licensee shall keep in his or her possession a signed statement from the employer containing the employers name, address, telephone number, and verification of employment and work hours. 
 Noregistration upload of files up to 250MB. Not available in some countries. GUIA DO PRAZER Tudo o que voc precisa saber sobre sexo est aqui Tornese um expert, aprenda com a experincia de outras pessoas. Download the free trial version below to get started. Doubleclick the downloaded file to install the software.
Noregistration upload of files up to 250MB. Not available in some countries. GUIA DO PRAZER Tudo o que voc precisa saber sobre sexo est aqui Tornese um expert, aprenda com a experincia de outras pessoas. Download the free trial version below to get started. Doubleclick the downloaded file to install the software. 

 DJ JUS FLOW. 1,814 likes 51 talking about this. REMEMBER your party aint hype unless its DATZ HYPE promo video 2. Managing Cash and the Cash Flow Statement. Online video clip. Managing Cash and the Cash Flow Statement 2016. Remember, a decrease in a non. At the Main menu go to Special Features and highlight the Main Menu entry. Then using your remote control press the Right arrow key to highl., Hustle Flow DVD. My Website https julianball. My 5. 0k Graphics Pack https youtu. QYSUAl. EMMy 3. 0k Graphics Pack https youtu. R2. 4z. TDss. My 2. Flow is the mental state of being completely immersed in an activity. Learn more about how flow works and some of the benefits of this mental state. K Banner Templates https youtu. Te. 6Es. VDSYEMy 1. K Graphics Pack https youtu. Lw. GILGv. Tyws. My 1. Graphics Pack https youtu. NRs. Zpv. IW7ns. Behance http www. Flow. Graphics. Creative Station http www. Creative. Station. Julian Ball Flow Graphics. Tags Flow, Graphics, Julian. Ball, Julian, Ball, Design, Speed art, Tutorial, Speedart, Photoshop, Illustrator, C4. D, speedart, giveaway, gfx, branding, logo, design, graphic, graphicdesign, youtube, banner, art, digital, vlog, video, film, australia, Adobe, Creative, graphics pack, flow graphics pack, gfx pack. Download free Flow stock video footage with 4k and HD clips. Joining Videvo gives you access to thousands of free stock footage clips. Remember Me social. Remember company flow Remember company flow Skip navigation Sign in. Mix Big juss and elp remember clip YouTube Bigg Jus talks New Solo Album. Movies All Video latest This Just In Prelinger Archives Democracy Now Occupy Wall Street TV NSA Clip Library. Flow Remember.
DJ JUS FLOW. 1,814 likes 51 talking about this. REMEMBER your party aint hype unless its DATZ HYPE promo video 2. Managing Cash and the Cash Flow Statement. Online video clip. Managing Cash and the Cash Flow Statement 2016. Remember, a decrease in a non. At the Main menu go to Special Features and highlight the Main Menu entry. Then using your remote control press the Right arrow key to highl., Hustle Flow DVD. My Website https julianball. My 5. 0k Graphics Pack https youtu. QYSUAl. EMMy 3. 0k Graphics Pack https youtu. R2. 4z. TDss. My 2. Flow is the mental state of being completely immersed in an activity. Learn more about how flow works and some of the benefits of this mental state. K Banner Templates https youtu. Te. 6Es. VDSYEMy 1. K Graphics Pack https youtu. Lw. GILGv. Tyws. My 1. Graphics Pack https youtu. NRs. Zpv. IW7ns. Behance http www. Flow. Graphics. Creative Station http www. Creative. Station. Julian Ball Flow Graphics. Tags Flow, Graphics, Julian. Ball, Julian, Ball, Design, Speed art, Tutorial, Speedart, Photoshop, Illustrator, C4. D, speedart, giveaway, gfx, branding, logo, design, graphic, graphicdesign, youtube, banner, art, digital, vlog, video, film, australia, Adobe, Creative, graphics pack, flow graphics pack, gfx pack. Download free Flow stock video footage with 4k and HD clips. Joining Videvo gives you access to thousands of free stock footage clips. Remember Me social. Remember company flow Remember company flow Skip navigation Sign in. Mix Big juss and elp remember clip YouTube Bigg Jus talks New Solo Album. Movies All Video latest This Just In Prelinger Archives Democracy Now Occupy Wall Street TV NSA Clip Library. Flow Remember. 


 The legend of Zelda Breath of The Wild Free Download bisa dikatakan sebagai game pc terbaik diantara yang terbaik yang pernah ada dan tentunya kalian bisa. APK BARU Download aplikasi Android Gratis. Blog, Updated at 1 4. PMBlog, Updated at 1. AMBlog, Updated at 5 1. PMBlog, Updated at 1 3. AMBlog, Updated at 3 3.
The legend of Zelda Breath of The Wild Free Download bisa dikatakan sebagai game pc terbaik diantara yang terbaik yang pernah ada dan tentunya kalian bisa. APK BARU Download aplikasi Android Gratis. Blog, Updated at 1 4. PMBlog, Updated at 1. AMBlog, Updated at 5 1. PMBlog, Updated at 1 3. AMBlog, Updated at 3 3. -3.jpg)
 Microsoft. The fiercely competitive software giant is positioning its wares for cloud computing with software and services. The companys two cash cows operating. PMBlog, Updated at 6 1. AMBlog, Updated at 1. PMBlog, Updated at 2 3. PMBlog, Updated at 5 5. PMBlog, Updated at 2 2. PMBlog, Updated at 4 4.
Microsoft. The fiercely competitive software giant is positioning its wares for cloud computing with software and services. The companys two cash cows operating. PMBlog, Updated at 6 1. AMBlog, Updated at 1. PMBlog, Updated at 2 3. PMBlog, Updated at 5 5. PMBlog, Updated at 2 2. PMBlog, Updated at 4 4. 
 Je word er heel suf en blij van. Cocane wordt gehaald uit de cocaplant. De cocaplant is een struik die op de Andesgebergte groeit in Zuid Amerika. De bekendste coca soorten zijn Erythroxylon coca en Erytroxylon novogranatense. In deze coca bladeren zit 1 cocaine. XTCMDMA is de chemische stof die zijn werk doet in XTC. Dus als we het over XTC hebben hebben we het ook over MDMA. MDMA heeft een oppeppende werking en heeft een bewustzijns veranderend effect. Dat betekent dat je je niet bewust bent van iets. Dat effect is verliefdheid en je hebt veel behoefte aan contact met andere. XTC word verkocht in de vorm van pillen poeder en kristallen. Wat doen drugs met je Wat drugs met je doen licht eraan welke soort drugs je gebruikt. De meest voorkomende bijwerkingen zijn dit Snellere hartslag, oververhitting waar je dood aan kan gaan, droge mond, nier, hart en leverstoornissen, watervergiftiging, epileptische aanvallen, serotoninesyndroom, verwardheid, hoofdpijn, stijve spieren en duizeligheid. Uiteindelijk kun je in het ziekenhuis op de Intensive Care belanden of zelfs doodgaan en dat allemaal doordat je verslaafd werd aan drugs. Drugs in je lichaam. Drugs in je lichaam is een beetje hetzelfde als het vorige hoofdstuk maar dit is het voornamelijk. Lever, hart en nier stoornissen. Drugs zijn zeer schadelijk voor je lever, waarom Omdat de lever schadelijke stoffen uit je lichaam haalt. In drugs zitten zeer schadelijke stoffen. Van teveel schadelijke stoffen raakt je lever overstuur en word zogezegd onschadelijk gemaakt. De sociale gevolgen van drugs. Als mensen verslaafd raken aan drugs geven ze er alles voor op, familie, vrienden echt alles ze verspillen zelfs duizenden euros en het maakt ze niks uit als ze maar drugs binnen krijgen. Ze beloven hun vrienden te stoppen ze zijn wanhopig maar ze vragen om geld en van dat geld kopen ze drugs. Sommige willen niks meer met hemhaar te maken hebben. Maar sommige willen hemhaar juist helpen, maar vaak helpt het niet. Meestal landen ze in het ziekenhuis en overleven ze het niet. Beroemdheden en drugs. Veel beroemdheden zijn overleden aan drugs meestal vanwege verdriet en kwaadheid dit zijn wat beroemdheden die zijn overleden aan drugs. Kurt Cobain, muzikant. Nick Drake, muzikant. Brian Epstein, manager van The Beatles. John Entwistle, muzikant van The Who. Chris Farley, acteur. Rainer Werner Fassbinder, filmregisseur. Judy Garland, actrice. Tim Hardin, muzikant. Jimi Hendrix, muzikant. Billie Holiday, zangeres. Michael Jackson, zanger. Janis Joplin, muzikant. Heath Ledger, acteur. Sonny Liston, wereldkampioen boksen. Marilyn Monroe, actrice. Keith Moon, muzikant, drummer van The Who. Jim Morrison, muzikant. Marco Pantani, wielrenner. Gram Parsons, muzikant. River Phoenix, acteur. Rob Pilatus, zanger o. Milli Vanilli. Edgar Allan Poe, schrijver mogelijkElvis Presley, muzikant. Dee Dee Ramone, muzikant van de Ramones. Tom Simpson, wielrenner. Hillel Slovak, muzikant van Red Hot Chili Peppers. Anna Nicole Smith, actrice. Layne Staley, muzikant. Ike Turner, muzikant, bandleider, talentscout. Sid Vicious, muzikant. Mike Von Erich, professioneel worstelaar. Andrew Wood, muzikant. Whitney Houston, zangeres. Amy Winehouse, zangeres. Afkickkliniek. Een afkickkliniek is een plek voor mensen die verslaafd zijn aan drugs. Op die plek kunnen ze afkicken van drugs je krijgt een speciale behandeling en ze proberen je daar thuis te laten voelen. Soms blijf je maar een paar weken in een afkickkliniek maar sommige wel een paar jaar. Als je in een afkickkliniek komt dan krijg je methadon. Methadon is een vervangingsmiddel dat herone vervangt. In de Hoop in Dordrecht zijn drugs alcohol sigaretten en slaapmiddelen streng verboden. In de Hoop is er veel te doen je hebt er een boerderij een broodjeszaak een muziekwinkel en een werkplaats. De aanpak van de Hoop werkt heel goed een op de drie verslaafden maakt het programma af en blijft clean. Dit was mijn spreekbeurt over drugs. Ik hoop dat jullie er wat van geleerd hebben.
Je word er heel suf en blij van. Cocane wordt gehaald uit de cocaplant. De cocaplant is een struik die op de Andesgebergte groeit in Zuid Amerika. De bekendste coca soorten zijn Erythroxylon coca en Erytroxylon novogranatense. In deze coca bladeren zit 1 cocaine. XTCMDMA is de chemische stof die zijn werk doet in XTC. Dus als we het over XTC hebben hebben we het ook over MDMA. MDMA heeft een oppeppende werking en heeft een bewustzijns veranderend effect. Dat betekent dat je je niet bewust bent van iets. Dat effect is verliefdheid en je hebt veel behoefte aan contact met andere. XTC word verkocht in de vorm van pillen poeder en kristallen. Wat doen drugs met je Wat drugs met je doen licht eraan welke soort drugs je gebruikt. De meest voorkomende bijwerkingen zijn dit Snellere hartslag, oververhitting waar je dood aan kan gaan, droge mond, nier, hart en leverstoornissen, watervergiftiging, epileptische aanvallen, serotoninesyndroom, verwardheid, hoofdpijn, stijve spieren en duizeligheid. Uiteindelijk kun je in het ziekenhuis op de Intensive Care belanden of zelfs doodgaan en dat allemaal doordat je verslaafd werd aan drugs. Drugs in je lichaam. Drugs in je lichaam is een beetje hetzelfde als het vorige hoofdstuk maar dit is het voornamelijk. Lever, hart en nier stoornissen. Drugs zijn zeer schadelijk voor je lever, waarom Omdat de lever schadelijke stoffen uit je lichaam haalt. In drugs zitten zeer schadelijke stoffen. Van teveel schadelijke stoffen raakt je lever overstuur en word zogezegd onschadelijk gemaakt. De sociale gevolgen van drugs. Als mensen verslaafd raken aan drugs geven ze er alles voor op, familie, vrienden echt alles ze verspillen zelfs duizenden euros en het maakt ze niks uit als ze maar drugs binnen krijgen. Ze beloven hun vrienden te stoppen ze zijn wanhopig maar ze vragen om geld en van dat geld kopen ze drugs. Sommige willen niks meer met hemhaar te maken hebben. Maar sommige willen hemhaar juist helpen, maar vaak helpt het niet. Meestal landen ze in het ziekenhuis en overleven ze het niet. Beroemdheden en drugs. Veel beroemdheden zijn overleden aan drugs meestal vanwege verdriet en kwaadheid dit zijn wat beroemdheden die zijn overleden aan drugs. Kurt Cobain, muzikant. Nick Drake, muzikant. Brian Epstein, manager van The Beatles. John Entwistle, muzikant van The Who. Chris Farley, acteur. Rainer Werner Fassbinder, filmregisseur. Judy Garland, actrice. Tim Hardin, muzikant. Jimi Hendrix, muzikant. Billie Holiday, zangeres. Michael Jackson, zanger. Janis Joplin, muzikant. Heath Ledger, acteur. Sonny Liston, wereldkampioen boksen. Marilyn Monroe, actrice. Keith Moon, muzikant, drummer van The Who. Jim Morrison, muzikant. Marco Pantani, wielrenner. Gram Parsons, muzikant. River Phoenix, acteur. Rob Pilatus, zanger o. Milli Vanilli. Edgar Allan Poe, schrijver mogelijkElvis Presley, muzikant. Dee Dee Ramone, muzikant van de Ramones. Tom Simpson, wielrenner. Hillel Slovak, muzikant van Red Hot Chili Peppers. Anna Nicole Smith, actrice. Layne Staley, muzikant. Ike Turner, muzikant, bandleider, talentscout. Sid Vicious, muzikant. Mike Von Erich, professioneel worstelaar. Andrew Wood, muzikant. Whitney Houston, zangeres. Amy Winehouse, zangeres. Afkickkliniek. Een afkickkliniek is een plek voor mensen die verslaafd zijn aan drugs. Op die plek kunnen ze afkicken van drugs je krijgt een speciale behandeling en ze proberen je daar thuis te laten voelen. Soms blijf je maar een paar weken in een afkickkliniek maar sommige wel een paar jaar. Als je in een afkickkliniek komt dan krijg je methadon. Methadon is een vervangingsmiddel dat herone vervangt. In de Hoop in Dordrecht zijn drugs alcohol sigaretten en slaapmiddelen streng verboden. In de Hoop is er veel te doen je hebt er een boerderij een broodjeszaak een muziekwinkel en een werkplaats. De aanpak van de Hoop werkt heel goed een op de drie verslaafden maakt het programma af en blijft clean. Dit was mijn spreekbeurt over drugs. Ik hoop dat jullie er wat van geleerd hebben. 
 Source 3wDrv100 Type Warning Description The 3ware Escalade Service should be removed ltnumber 1 Comment for event id 2 from source 3wDrv100 Source acvpnagent. Jobs earlier question to Sidhu had already sparked a number of ideas. When Apple. Net was cancelled in October, Sidhu led an effort to develop a new networking system based on the Apple. Bus hardware. This new system would not have to conform to any existing preconceptions, and was designed to be worthy of the Mac a system that was user installable, had zero configuration, and no fixed network addresses in short, a true plug and play network. third party source needed Considerable effort was needed, but by the time the Mac was released, the basic concepts had been outlined, and some of the low level protocols were on their way to completion. Sidhu mentioned the work to Belleville only two hours after the Mac was announced. 4The new Apple. Bus was announced in early 1. N 1 allowing direct connection from the Mac or Lisa through a small box that plugged into the serial port and connected via cables to the next computer upstream and downstream. Adaptors for Apple II and Apple III were also announced. 1. Apple also announced that Apple. Bus networks could be attached to, and would appear to be a single node within, a Token Ring system. Details of how this would work were sketchy. Apple. TalkeditJust prior to its release in early 1. Apple. Bus was renamed Apple. Talk. The system had a number of limitations, including a speed of only 2. LAN. But as the basic hardware was built into the Mac, adding nodes only cost about 5. In comparison, Ethernet or Token Ring cards cost hundreds or thousands of dollars. Additionally, the entire networking stack required only about 6 k. B of RAM, allowing it to run on any Mac. The relatively slow speed of Apple. Talk allowed further reductions in cost. Instead of using RS 4. Apple. Talk Personal Network cabling used a single common electrical ground, which limited speeds to about 5. This meant that common three conductor cables could be used for wiring. Additionally, the adaptors were designed to be self terminating, meaning that nodes at the end of the network could simply leave their last connector unconnected. There was no need for the wires to be connected back together into a loop, nor the need for hubs or other devices. The system was designed for future expansion the addressing system allowed for expansion to 2. LAN although only 3. LANs into larger collections. Zones allowed devices to be addressed within a bridge connected internet. Additionally, Apple. Talk was designed from the start to allow use with any potential underlying physical link. The main advantage of Apple. Talk was that it was completely maintenance free. To join a device to a network, you simply plugged the adaptor into the machine, then connected a cable from it to any free port on any other adaptor. Apple. Talks internal protocols negotiated a working network address number, automatically gave the computer a human readable name, and collected up a list of the names and types of other machines on the network so the user could browse the devices through the GUI based Chooser. Apple. Talk was so easy to use that ad hoc networks tended to appear whenever multiple Macs were in the same room. 1. Apple would later use this in an advertisement showing a network being created between two seats in an airplane. 1. Phone. Net and other adaptorseditA thriving 3rd party market for Apple. Talk devices developed over the next few years. One particularly notable example was an alternate adaptor designed by BMUG and commercialized by Farallon as Phone.
Source 3wDrv100 Type Warning Description The 3ware Escalade Service should be removed ltnumber 1 Comment for event id 2 from source 3wDrv100 Source acvpnagent. Jobs earlier question to Sidhu had already sparked a number of ideas. When Apple. Net was cancelled in October, Sidhu led an effort to develop a new networking system based on the Apple. Bus hardware. This new system would not have to conform to any existing preconceptions, and was designed to be worthy of the Mac a system that was user installable, had zero configuration, and no fixed network addresses in short, a true plug and play network. third party source needed Considerable effort was needed, but by the time the Mac was released, the basic concepts had been outlined, and some of the low level protocols were on their way to completion. Sidhu mentioned the work to Belleville only two hours after the Mac was announced. 4The new Apple. Bus was announced in early 1. N 1 allowing direct connection from the Mac or Lisa through a small box that plugged into the serial port and connected via cables to the next computer upstream and downstream. Adaptors for Apple II and Apple III were also announced. 1. Apple also announced that Apple. Bus networks could be attached to, and would appear to be a single node within, a Token Ring system. Details of how this would work were sketchy. Apple. TalkeditJust prior to its release in early 1. Apple. Bus was renamed Apple. Talk. The system had a number of limitations, including a speed of only 2. LAN. But as the basic hardware was built into the Mac, adding nodes only cost about 5. In comparison, Ethernet or Token Ring cards cost hundreds or thousands of dollars. Additionally, the entire networking stack required only about 6 k. B of RAM, allowing it to run on any Mac. The relatively slow speed of Apple. Talk allowed further reductions in cost. Instead of using RS 4. Apple. Talk Personal Network cabling used a single common electrical ground, which limited speeds to about 5. This meant that common three conductor cables could be used for wiring. Additionally, the adaptors were designed to be self terminating, meaning that nodes at the end of the network could simply leave their last connector unconnected. There was no need for the wires to be connected back together into a loop, nor the need for hubs or other devices. The system was designed for future expansion the addressing system allowed for expansion to 2. LAN although only 3. LANs into larger collections. Zones allowed devices to be addressed within a bridge connected internet. Additionally, Apple. Talk was designed from the start to allow use with any potential underlying physical link. The main advantage of Apple. Talk was that it was completely maintenance free. To join a device to a network, you simply plugged the adaptor into the machine, then connected a cable from it to any free port on any other adaptor. Apple. Talks internal protocols negotiated a working network address number, automatically gave the computer a human readable name, and collected up a list of the names and types of other machines on the network so the user could browse the devices through the GUI based Chooser. Apple. Talk was so easy to use that ad hoc networks tended to appear whenever multiple Macs were in the same room. 1. Apple would later use this in an advertisement showing a network being created between two seats in an airplane. 1. Phone. Net and other adaptorseditA thriving 3rd party market for Apple. Talk devices developed over the next few years. One particularly notable example was an alternate adaptor designed by BMUG and commercialized by Farallon as Phone. 


 Hidden Object Games Free Download. Collection of free full version games for computer and PC. Hidden Object Games Free Download and play for free. Free Download For PC Windows. Hidden Object Games Free Download Full Version With No Time Limits For PC. Great collection of free full version Hidden Object games for. Hidden object games are an exciting collection of mysterious puzzle solving casual games that are very popular with childrens and adults alike. The games are all. Play free game downloads. Big Fish is the 1 place to find casual games Safe secure. Games for PC, Mac Mobile. No waiting. Helpful customer service
Hidden Object Games Free Download. Collection of free full version games for computer and PC. Hidden Object Games Free Download and play for free. Free Download For PC Windows. Hidden Object Games Free Download Full Version With No Time Limits For PC. Great collection of free full version Hidden Object games for. Hidden object games are an exciting collection of mysterious puzzle solving casual games that are very popular with childrens and adults alike. The games are all. Play free game downloads. Big Fish is the 1 place to find casual games Safe secure. Games for PC, Mac Mobile. No waiting. Helpful customer service